 |
||
|
||
| ||
USR8200 settingsUSR8200 router has two configuration interfaces – via web browser and telnet. Graphical web interface will be described later, and now I'll dwell upon the console interface, which can be accessed via telnet. According to the help, there are quite many console commands. So if you wish, you'll probably manage to configure the device using console (at least to perform minimal configuration to get access to the web interface). One command in this help interested me personally - shell.
It turned out that there is another shell within the console interface. What can it do? The message displayed on the screen Voila! We are really under Unix (Linux) like operating system with the sh shell. By the way, this shell helped me to solve the problem with IPSec connections: at first I couldn't connect to USR8200 VPN server: the connection was sort of established but packets wouldn't go through the created tunnels. It turned out (you can see that from the output of the whack command) that even if two computers connected with a tunnel are in the same subnetwork (192.168.0.0/24), the implementation of the connection establishment procedure from U.S.Robotics engineers tries to send IPSec packets via default gw (default gateway for WAN port), though in this case it shouldn't have been done. Of course, it wasn't working! I wonder, how many similar pitfalls one can encounter when using this device? You see, the more complex is the system, the higher is the probability that some part of the system will fail. OK, shell works. Of course, there are not so many utilities in there, but theoretically, you can mount an external USB storage device with lacking programs. They will have to be compiled not for the x86 architecture though... Now let's proceed to the web interface of the device management. After you enter password, you get to the network map screen. Quite a good idea to my mind – on this map you can see all devices presently connected to USR8200 (by connected I mean active connections to VPN server or a data storage). What concerns the rest... yes, the interface is rich with settings, but to my mind its creators made it a bit too complicated. On the one hand, it's full of wizards, which facilitate the configuration process. On the other hand, even if you need advanced configuration options, you will have to complete the wizard anyway. You cannot open advanced options without completing a wizard. Besides (to my subjective mind) the interface is not quite logical. The same settings can be reached from different points, that is you cannot simply walk through all the settings one by one (you may get lost). On the other hand, walking through the interface for several days (performing my tests) I got used to it and didn't feel its "lack of logic" any more. On the whole, the interface is flexible and provides access to many settings, but I have come across better implementations (of the interface, but not of the configuration options). Traditionally, we are going to publish screenshots of major interface sections with minimal comments (device features have been previously presented in the summary table and I think that describing what you can see on the screenshots with your own eyes is just a waste of time). The Network Connections section lists all interfaces (lan, wan, vpn), which are presently available in the device. You can also add new interfaces and configure the existing ones here. LAN and WAN interfaces have a lot of settings including manual MTU size, additional IP addresses (ip-aliasing), routing table setup, firewall activation, etc. Additional interfaces (or modification of the functionality of the existing ones) are added using a special wizard. The Security tabbed sheet manages various filters of the device. In the first section you can specify policies of the embedded firewall. In the second – you can create your own firewall rules (in addition to the selected policy). The rules are created in the following way. You type an IP address (there is an option to select "block for the entire network") and select the check boxes with the rules, which will block the traffic to the selected IP address. The list contains a lot of preset rules (several screens, the screenshot displays only the top of the list) of protocol filtering. Besides, you can also add your own rules to the list. Rule descriptions are very flexible – you can define practically any rule you need. By the way, this is a common list (with preset and custom rules), which is used in other sections as well. BUT. Yes, there is always this "BUT". I was surprised to find out that (having selected the "block all" policy) I cannot add "allow" rules in this section (Access Control). Someone had obviously worked on the simplification of the configuration process. It turned out that my example can also be implemented, but not in this section (though the opposite would have been more logical). In Local Servers you can configure virtual servers. The rules that specify which ports can be routed to LAN are taken from the common list configured in the previous section. In Remote Administration you can configure permissions for remote (via WAN) device control, SNMP activation, as well as ICMP echo request. It's interesting that WAN port echo activation actually changed nothing – USR8200 wouldn't respond to pings anyway. The Advanced Filtering subsection at last reveals the entire wealth of features of the embedded firewall. Here you can configure any permissions or blocks for the rules as well as use SPI features, that is build rules not only for one packet but for all packets pertaining to the same connection. The rules themselves are built in the same way as in Access Control. The Security Log subsection displays event logs and allows to configure logging. To my mind, this logging section (there is another logging section, we'll describe it later) provides little information – it logs user authorizations as well as (if activated in settings) connections to the device (the latter will deluge all the logs, you can see that on the screenshot below). On the other hand, this section also gets firewall rule logs, if the rules are configured correspondingly. The data amount is actually large, but the impossibility to store logs on the external syslog server greatly reduces its significance. The Restrictions section is used to configure web traffic filtering. Namely, domain filtering. Unfortunately, the interface supports only full web site names, it does not support any masking. It's impossible to block Java and ActiveX content. I also didn't manage to find integration options with external content filtering services. Besides, all the restrictions mentioned above apply to all users globally – you cannot configure different rules for different IP addresses. Advanced section. It contains tabbed sheets to access most of the previous settings and a large number of new ones. Dynamic DNS allows to configure cognominal services. The list of services compatible with this device is impressive (the screenshot contains only half of the list). The next subsection allows to activate the embedded DNS server. It can be activated not only on LAN but on WAN interface as well. In the Routing section you can configure routing tables for the interfaces. 
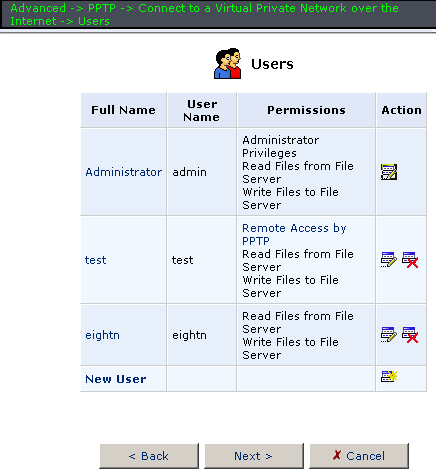
 In the Users section you can configure users' logins and passwords as well as their access levels. The list of users is utilized for the USR8200 configuration interface authorization, access to FTP and SMB file servers, as well as for VPN PPTP server authorizations. The Certificates section is used to store and generate certificates. Unfortunately, this router cannot work with Radius and similar services, so you'll have to load certificates manually.  Date and Time configures the internal clock as well as its synchronization modes.  The next section allows to check for updates and update the firmware. Note that you can configure notifications on the new available versions and even configure autoupdating the firmware. 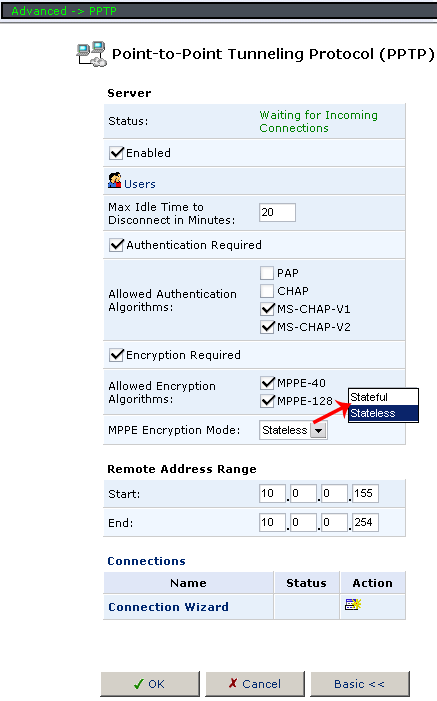
  In PPTP you can configure the VPN PPTP server. Or the PPTP client mode for WAN interface. 
 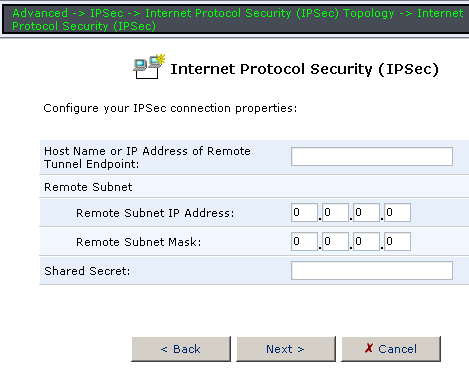 The IPSec section is devoted to the IPSec server configuration. IPSec has a great number of options and modes. You can even increase the detail level for IPSec connection logs. In System Settings you can configure several SMB file server options, etc. In the next section – FTP server modes. 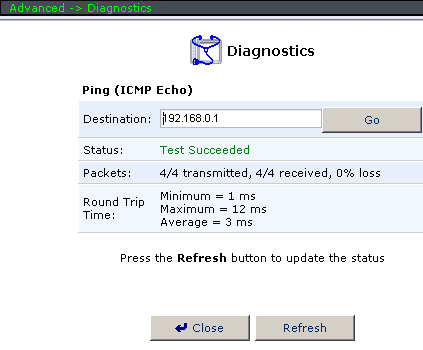 In Diagnostics you can ping a remote host directly from USR8200. In System Monitoring you can browse various parameters of the existing interfaces as well as the amount of sent/received traffic via these interfaces. You can also see system logs of the device here. By the way, speaking of integration with external data storage systems. Via Network Map you can see connected storage systems, access them and check the integrity of their file systems or format storage media. Navigation:
Evgeniy Zaitsev (eightn@ixbt.com) 24 August, 2004 Write a comment below. No registration needed!
|
Platform · Video · Multimedia · Mobile · Other || About us & Privacy policy · Twitter · Facebook Copyright © Byrds Research & Publishing, Ltd., 1997–2011. All rights reserved. |