 |
||
|
||
| ||
 Home routers are getting more popular nowadays. It's not surprising because at a relatively low price you get a "black box" capable of many interesting things. First of all, it provides an Internet access for a small local network. I called it black because it's unclear what happens inside it at a particular moment. You can just guess or monitor the device via SNMP and then (mostly in expensive models) learn additional information from log files. Undoubtedly, each problem has several solutions. And instead of such router we can use a usual computer with two network cards. This computer connects a switch and the Internet. It's also possible to realize such router under OSes of the Windows family. But hardly anyone would take the risk of entrusting these operating systems with the Internet access task, especially if the computer has an external IP address (and therefore, will be easily accessible from outside). That is why protection of such router will be in the first place. Can the Windows 98 SE provide any protection? Hardly. Moreover, the system requirements of these OSes for the hardware have never been low. However, this method is easy to realize: there are a lot of experts in the Windows. Moreover, you might not need special skills as there is Internet Sharing. It's quite another matter to use OSes of the Unix or Linux families. They have very low system requirements, for example, a computer based on the Pentium 100 MHz with 16 MB RAM, a hard drive of 200-300 MB and a couple of network cards of 10 Mbit will be enough for most cases of connection of a small local network to the Internet. Isn't the price attractive? Note that the above computer is not the cheapest solution; you can use even a 486-based machine. Apart from a cheap platform and free software, there is one more advantage, namely a more flexible configuration system, in particular, network protection and firewall, a convenient way of the Internet access mediation, higher stability (compared to Windows platforms). Besides, you can couple the router with such things as a DNS server, transparent (for the local network) traffic proxying, e-mail server, remote control of the computer via SSH (encrypted connection) etc. It's clear that all that stuff shouldn't be put onto the shoulders of a machine which works as a primary firewall and a router into the external network. But it's just an example. All these things will work nicely on a Pentium-level machine for a local network of about 20-30 people. But you should expand the memory up to 32-64MB and the HDD size up to 1-2GB (first of all, it's necessary for a proxy server which eats a lot). You can easily imagine how the Windows would work on such machine even without additional services. But this approach also has drawbacks. The most obvious one is that it can't be a problem to find an expert in these OSes. Moreover, a router is based on a separate computer - the hardware such computers are assembled of is less reliable, at least because it has a hard drive which is a mechanical device. Of course, it's possible to replace it with a flash disc but the price will go up markedly. Finally, the unit is not small, consumes more power (compared with home routers) and produces more noise. That is why home routers enjoy the growing popularity. You don't need an expert to get the system up and running. Usually a manual provides the detailed instructions for the primary stage. In many cases this stage is sufficient. So, the whole adjustment process can take about half an hour. If it fails (which happens evidently more seldom compared to assembled computers, at least because of fewer components) you have the guarantee. These devices are especially popular in those networks which have no network administrators but an Internet access is needed. The principle of operation of most cheap devices is based on the NA[P]T technology (Network Address [and Port] Translation). The latter P is often omitted, though it would be more correct to speak about two technologies NAT and PAT - Network Address Translation and Port Address Translation. The technology works the following way. The device is given an external address on the external network (Internet) and the router translates all requests with addresses from the internal local network outside putting into the requests its external IP. The responses coming from outside will be converted back. So, a user working inside a local network doesn't notice a router and works as if it's on the Internet. From the standpoint of the external network (Internet), all requests are coming from the router (with the router's IP address), without any network behind it. Thus, a local network is protected from the outward access. That is why such solution is a good protection for all computers of a local network. Now about the shortcomings of the NAT. Not all applications like such a way of realization of the Internet access. For example, you can't connect FTP servers on the Internet in the active mode, transfer files via ICQ to another user etc. Also, you can't open an FTP server or set a client of a P2P network (e.g., eDonkey) for distribution of files. Just because you are not seen behind the router. However, most routers have settings to divert requests received at certain ports (e.g., 80 - WWW and 21 - FTP) to respective hosts inside a local network. That is why it's still possible to provide an outside access to internal servers. The NAT doesn't allow the IPSEC protocol which is used for establishing VPN networks or encrypted tunnels to work. You need a special revision of the NAT to support this protocol, which is not available in most router. Another downside of a common IP address of the network is that not all servers on the Internet like that different clients enter their sites from the same IP. Some voting systems wouldn't accept several votes from the same IP. Or, some companies limit the number of SMS messages that can be sent from the same IP. Now let's have a look at a home router marked ISB PRO800 Turbo from Nexland. It integrates a lot of advanced ideas, including the IPsec protocol support. The device costs $400 at the moment. It's not little, that is why let's see what we can get for this sum of money.  The router comes with an external power supply unit, a 3m cable of the 5th category, a Null Modem cable 90 cm long (that is why to configure the device in the control panel you must put it close to the computer), a CD with documentation (in English and French) and additional utilities and a printed version of the documentation (70 pages), a copy of the English PDF file. A VPN client Symantec RaptorMobile (with 10-user licenses) wasn't found here though it was mentioned on the site.   The device is packed into a metallic case. It's not big (140mm x 284 mm x 32 mm), that is why it can be put anywhere, even hung onto the wall. Its front panel houses:

 Back view:

 As you can see, the router is stuffed with loads of various functions. Now take a look at its specs.
Circuit design  
The WAN interfaces use popular Ethernet Realtek RTL8019AS controllers:  The specified performance (data transfer from LAN to WAN or back) is 8 Mbit. That is, when both ports are used (the theoretical speed of each is 10 Mbit), the overall performance doesn't exceed 8 Mbit. Probably, it's on account of the too slow memory interface. The router uses two 16-bit V54C316162VT6 memory chips, each of 16 Mbit. Both have 6ns access time, and the working frequency doesn't exceed 166 MHz. For analyzing a packet and defining its route the processor must read it from memory, analyze and, probably, change and write back. The same interface must be available for other devices as well, for example, a Fast Ethernet controller which translates packets from/into LAN. That is why the overall memory bandwidth is distributed among respective modules. And mostly likely, it's not enough for speedy data streams. Configuration menu.The Nexland PRO800 Turbo can be set up in the console (via the serial port of the terminal) and via the WEB interface. Here is the console:
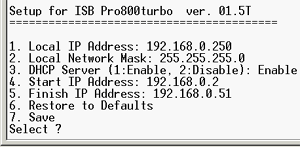 This is a root menu, there are no others. This option can be used only for restoring settings to default ones (or assigning an IP address) after an error in the WEB settings. The steps of setting up the router via the WEB interface are given in the guide. Besides, the interface is a breeze to use; it has tips on each configuration screen. The number of settings and ease of use are astounding. Let's dive into them. 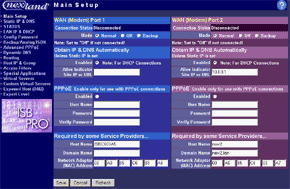 To connect the WEB interface you must enter http://192.168.0.1 in the browser (default address) and you will get into the configuration menu.
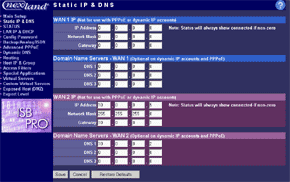 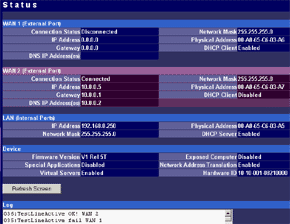 The main menu makes possible to change parameters of WAN interfaces such as IP addresses of interfaces and DNS servers, a mode of the interface (main or backup), enable PPPoE connection and change a MAC address of the interface (in the current firmware version the latter option didn't work - after changing the MAC address and rebooting the old MAC address was restored). And in the status menu you can look at the current status of WAN ports and main settings of the router. Here you can also find out the version of the installed OS (firmware), I used the last available version V1 Rel 5T. Modes of the WAN portsThe ISB 800PRO Turbo mode supports operation of both WAN interfaces in two different modes. And both WAN interfaces are connected to different communication lines (and probably, to different providers). Now about the load-balanced mode. If just one user works at the moment, the load hasn't to be balanced, as he/she uses one WAN interface. But if they are two or more, the balancing mechanism will distribute the users among the WAN interfaces. Thus, it's possible to reach an almost doubled throughput and use the bands of both communication lines the most optimal way. In this mode the overall speed can be higher than in case of a single interface (due to the limit to 8 Mbit). But even if both channels are not used entirely, we can benefit at least because pings of the packets are smaller with such balancing. It's possible to set maximum percentage for usage of the interfaces. By default, it's 50%. If necessary, you can bind the host from the LAN to a certain WAN interface, and it will always get into the external network through it. Ordinary users won't need it, but sometimes it can be useful for local servers visible from outside. The second mode of the WAN interface is a backup channel mode. In this case only one interface operates (by 100%), while the second is in the standby mode. If the first fails (it can be checked by pinging a certain host indicated in the configuration), the router will move the load onto the second interface. It's also possible to shift the load to the RS232 port with a modem connected (this mode can also be selected with DIP switches on the back). Thus, error-free operation of the channel is more secured - should one line fail (if the router is connected to one WAN) or both WAN lines fail (which is unlikely), you will have a low-speed Internet connection via a modem. It's clear that all tricks with two WAN interfaces are possible only for those who have two dedicated lines. There are not many such users out there. That is why the others should go with the ISB 800PRO which has only one WAN port. You can save about $100. DHCP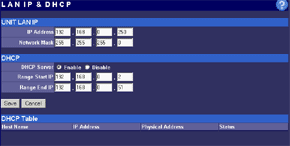 The Nexland PRO800 Turbo can receive necessary settings for its WAN interfaces from a provider and has an integrated DHCP server which allows assigning IP addresses to 253 hosts in the network. It's possible to bind IP addresses to MAC. Configuration access restriction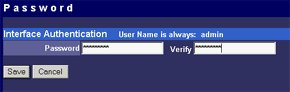 By default the router is not password protected. It should be immediately set up or you should restrict access to telnet and WEB interfaces for everyone except the administrator and authorized people, using access restrictions in the tab of expert options. SNMPThe router supports the SNMP protocol ver.1. The Simple Network Management Protocol allows checking different parameters of the device and current traffic in the real-time mode. You can also send SNMP messages (SNMP traps) to any host of your network. Dynamic DNS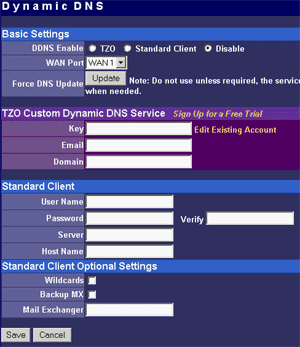 The Internet has a lot of services of the dynamic DNS. The documentation of the router describes operation with dyndns.org. These services are used if an IP address assigned to you is dynamic (i.e. it changes each time you connect the network). But if WWW or FTP servers are loaded you should use a static URL (domain name). Of course, you can forgo a static name, but how will others find your WWW server? It's not a good idea to inform all interested people about your new IP address. That is why an IP address for a static URL (for example, myhome.nexland.net) is changed by the dynamic DNS. After you have chosen a domain name and registered at one of the services of the dynamic DNS, you should configure the router so that information on your new IP address will be updated at the dynamic DNS service. After that your domain name will always indicate at the current IP address the router received during the last connection to the provider. Routing table.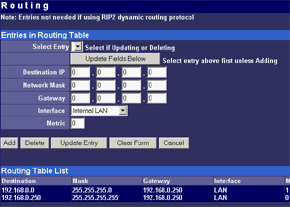 Nexland PRO800 Turbo lets you add routes manually in the routing table. Besides, it supports the RIP2 routing protocol. It builds routing tables on all network's routers automatically, provided that all routers support this protocol. That is why the ISB PRO800 Turbo can be used in larger networks divided into subnetworks by the routers. Hosts and groups.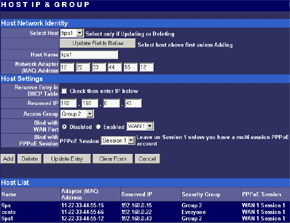 Here you can bind an IP address to MAC (which strengthens network security), provide a certain IP address only for a definite MAC address or bind a certain IP address to one of the WAN interfaces. Thus you can use a dedicated interface for an FTP server and leave the other for Internet-users so that the FTP server won't bother users. In the same section you can combine IP addresses of a group. Groups are used to arrange filtering. But they are 4 in all (plus "everyone"). It's not enough for a large network. Moreover, you can't put a range of IP addresses or a whole subnetwork into a group. You will have to list addresses one by one. Do you realize how much time it can take to enter 128 addresses into the second group? Access filters.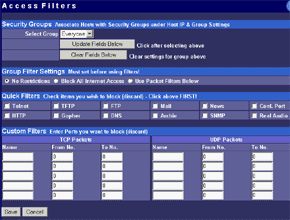 Using filters you can limit some groups of IP addresses to certain protocols or forbid the Internet access at all for them. For example, you can let workers of the first department use only e-mail and WEB. Apart from the specified protocols you can add 10 your own ones (5 for TCP and 5 for UDP) by setting a port address or their range. Unfortunately, the interface of handling the filters is far not convenient. All filtering rules can be set for groups. But we have only 4+1 groups. Besides, it's impossible to "forbid everything except...". Such model can be realized through user protocols, but it's not always possible either. Moreover, you can't fix time intervals for the filters, for example, forbid WWW and FTP only in the working hours. Virtual servers.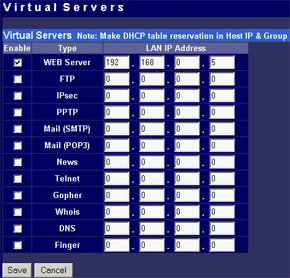 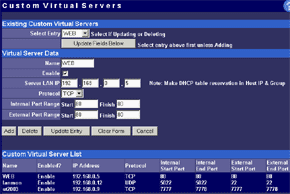 The mechanism of virtual ports can make a server located behind the router (in LAN) visible from the Internet. Usually, none of the LAN machines can be seen from the Internet. But in the virtual ports' menu you can assign a port (for example, 80 - WEB) on the router and an address/port inside the LAN to divert the request. Thus, an Internet user, when addressing an external address, sees a WEB server located on the 80th port of the router. In reality, the server is located on the LAN, behind the router. The WEB server on the LAN defines a request from the Internet and processes it a standard way. For virtual servers you can assign both predefined and your own ports. In the latter case you can set a range of ports. DMZ zone.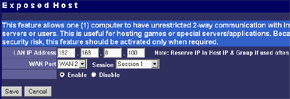 This option has both pros and cons. One of computers inside a local network can be exposed so that all its ports can be seen from the Internet. It can affect security but sometimes it must be done, for example, in case this computer has the IDS (Intrusion-Detection System). But in most cases you can do with features of virtual servers. Nonstandard applications.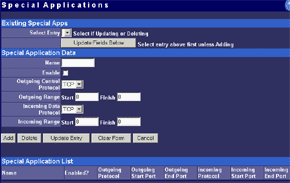 The router allows working with programs which use bidirectonal data exchange protocols. For this purpose you must set in the configuration ranges of the ports used in these protocols. The device provides operation only with low-speed protocols of this type. Expert options.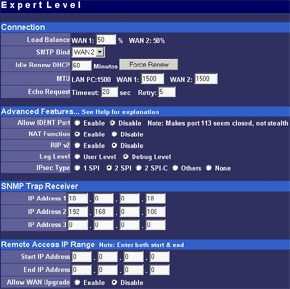 Here you can make settings for traffic balancing between WAN ports and assign SMTP (email) traffic to a certain WAN interface (it's useful if a provider which keeps your e-mail box permits an access to its SMTP server only from certain routes (for example, from a line connected to the WAN1)), change an MTU size for WAN interfaces and other options we mentioned above. Besides, by disabling the NAT function you can turn the Nexland PRO800 Turbo into a bridge. VPN support.The ISB PRO800 Turbo supports virtual private networks. Formally, the router can pump an unlimited number of IPsec/PPTP (IP Security/Point-to-Point Tunneling Protocol) tunnels, as well as one more L2TP session. But actually, their number is limited by the memory onboard. The above protocols are needed to build encrypted connections between end hosts or networks via the Internet. But they can't work with the NAT due to their specific character. However, Nexland modified the NAT mechanism. Note that the router can only support VPN sessions; it is not a server of IPsec or other protocols. Most routers of this class can work with just one protected session. On the other hand, a local network doesn't send often more than one VPN tunnel. Well, just remember that a VPN is not a cure-all. If set up incorrectly, the due security won't be provided. For example, using this tunnel you can get into a protected network using holes in security of a network located on the other end of the encrypted tunnel. In the router's configuration you can set different types of the IPsec protocol, including the "other" type which is used when the protocol doesn't work with the NAT. In this case the IPsec server is taken into the DMZ zone. I checked operability of the FreeS/WAN (IPSEC and IKE under Linux) with the router and everything proved to work flawlessly. Testing techniqueTestbeds (2 computers):
One of the computers was connected to the local network (i.e. to the router's local port), and the other to the external network (to the WAN port). The tested device was put between them. Then we started up the traffic generators and took the measurements. This way we estimated throughput of the router. The integrated switch (for 8 ports) wasn't tested as its speed is higher than the routing rate. For traffic generation and readout we used the Iperf 1.62. Each test was carried out 15 times and then the best result (in speed) was selected. The second utility we used was netPIPE 2.4. The program generates traffic with a gradually increasing data packet (a packet of size N is transferred several times, the number is inversely proportional to the size but not less then 7). This scheme can show you percentage of the channel utilization relative to the size of data transferred. Startup parameters for Iperf:
Startup parameters for netPIPE:
Test resultsIperf results.
To some reason, the traffic rate from the external network into the LAN is twice as low as into the WAN. The total speed doesn't catch up with the specified one, probably because of the improper traffic generation program. NetPIPE results. 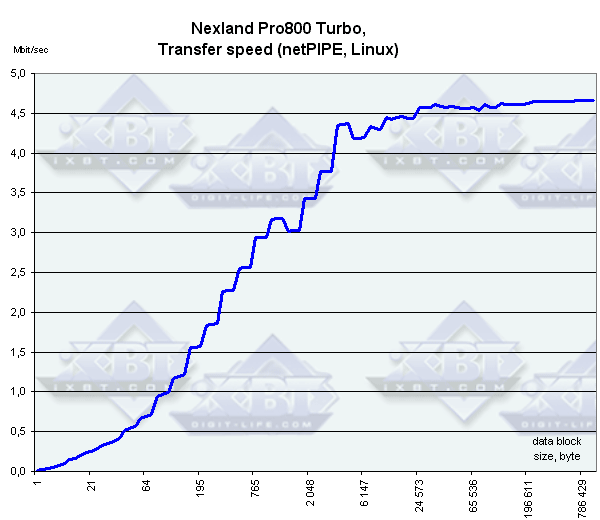 Again the transfer speed is lower than the indicated in the specs, but it's still enough for most dedicated lines. Security testIn this test we used a freeware network security scanner Nessus 1.2.6. We scanned the external WAN port with all available plugins from the list. No problems were noticed. However, it doesn't mean they will never crop up. On the other hand, problems can arise mainly because of flaws in realization of the TCP/IP stack. But the developers at Nexland have given this realization a very thorough thought. ConclusionThe Nexland ISB Pro800 Turbo will please many. It's crammed with various features. The only weak point (though many would hardly even give it a thought) is an inconvenient and scant integrated firewall which controls access of local clients. For many the filtering means the router provides will be sufficient. Highs
Lows
Evgeniy Zaycev (eightn@ixbt.com)
Write a comment below. No registration needed!
|
Platform · Video · Multimedia · Mobile · Other || About us & Privacy policy · Twitter · Facebook Copyright © Byrds Research & Publishing, Ltd., 1997–2011. All rights reserved. |