 |
||
|
||
| ||
Computer security has become one of the most important problems in the IT sphere. Various complex systems of computer security and tools available to OS and software developers allow to protect the IT infrastructure of an enterprise from external attacks. Enterprise environment security tools have advanced far forward of late. But the problem of insider attacks is one of the most burning issues now. Enterprises have to spend a lot of time and effort to develop complex security policies for workstations and servers used by various groups of employees. A significant progress in virtualization technologies allows many companies to cut down expenses on maintaining IT infrastructures of desktop and server platforms by consolidating several virtual machines on a single physical computer. Virtual systems can be integrated into the enterprise environment to raise IT efficiency of the company. However, just like physical platforms (or even more), they require much attention as far as their security is concerned. VMware is one of the first companies to take care of virtualization security and protected environments. The first product of this company to solve these problems for workstations was VMware ACE 1.0. It allowed to create secure virtual machines and use them as work environments for employees as well as to demonstrate software and to train staff. However, the product lacked many features for corporate use, such as centralized deployment and integration with other virtualization platforms from VMware. So it did not become very popular. The second version of VMware ACE released in Q2 2007 got so many new features that many companies will certainly use it to create secure virtual environments. About VMware ACE 2.0VMware released the second version of VMware ACE simultaneously with VMware Workstation 6 for a reason: VMware ACE is an extension of Workstation with additional features to create secure computing environments. ACE Option Pack can be included into VMware Workstation 6 by entering a license key for VMware ACE. Key features of the product: Centralized policy-based management.That is you can control virtual machines from the ACE Management Server with the following features:
Strong securityProtect sensitive and proprietary information with robust security features such as full-volume encryption and granular access control over all network and peripheral ports.
Flexible deploymentVMware ACE can be used to create environments, which can be distributed on any media and deployed to workstations in a centralized manner. It's very easy:
VMware ACE ApplicationsVMware ACE can be used in various aspects, when you must protect vital information in virtual machines, stave off unauthorized data copying, and secure environments from a single place. Main applications of VMware ACE:
How VMware ACE WorksVMware ACE allows to deploy and service packages consisting of a virtual machine, security and access policies from the ACE Management Server. You can automatically update virtual desktops and deactivate them when necessary. That's how the general VMware ACE usage diagram looks like: 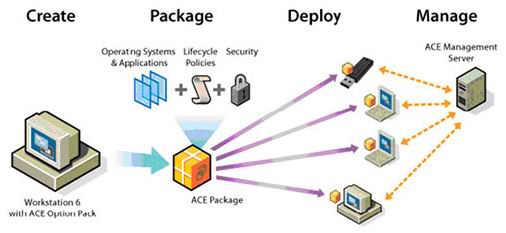 Using VMware ACE Here is a step-by-step procedure of deploying VMware ACE virtual environments:
VMware ACE EditionsVMware offers three editions of VMware ACE: Starter, Standard, and Enterprise. The last two editions are licensed with Volume License Key - you enter the license key and automatically include licenses into created packages. It's very convenient for mass deployment of packages. The table below lists features of each edition.
Installation and Setup of Virtual Environments in VMware ACEAfter you install VMware Workstation 6 in the host operating system, you should enter the license key to unlock VMware ACE. Restart the product. You will see a new VMware ACE window, where you can still create regular virtual machines. In order to create a new virtual secure ACE environment, choose New->ACE Master in the File menu. You will see the following window: 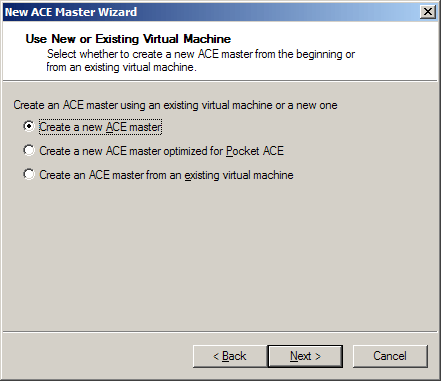 Creating an secure ACE Master environment Then you should specify the same settings as in VMware Workstation. But a virtual machine cannot use a physical hard disk directly. Virtual environments use NAT (Network Address Translation) as the safest option by default. So secure virtual machines can connect to an external network, while other computers in the external network cannot connect to them. After a virtual machine is created, you should install a guest OS and VMware Tools. Then you can get busy with environment policies. Just choose Edit policies in the main window. 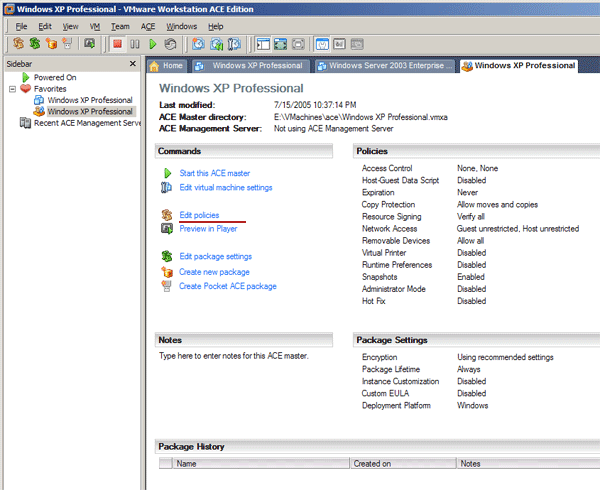 VMware ACE. Main window. You will see the following window:  Configuring policies for ACE environments You can control various parameters of access policies and environment security in the following aspects: - Access Control - Host-Guest Data Script - Expiration - Copy protection - Resource Signing - Network Access - Removable Devices and USB Devices - Virtual Printer - Runtime Preferences - Snapshots - Administrator mode - Hot Fix
This mechanism is very convenient for mass deployment of virtual machines. After your policies are specified, you must configure the package, which will be created from various components of an secure virtual environment. Click Edit package setting in the main VMware ACE window.  Editing VMware ACE package settings In this window a system administrator can prepare a package with a virtual machine for deployment:
After a package is properly configured, a system administrator must create a ready-for-deployment package of one of two types: to be used on a hard drive or to be recorded on a removable medium using Pocket ACE. To create a package of the first type, click Create new package in the main VMware ACE window. Then you should type a package name, location of its files, and notes. Then you will be prompted to choose on of three options:
Choose Custom and select necessary components.  Selecting package contents A package may include:
The Disk Space panel also shows package size and free space required to deploy a virtual environment. After a packages is created, it can be deployed on workstations or servers for VDI (Virtual Desktop Infrastructure). If there aren't many of them, you can do without centralized control. However, if you create a lot of secure environments, which are transferred from computer to computer, you'll need constant control and centralized security policy updates. VMware ACE Management ServerACE Management Server from VMware is a powerful tool to maintain an enterprise desktop infrastructure. Main functions of ACE Management Server include the following:
ACE Management Server is distributed as an installation package for Windows and Linux host systems, as well as a virtual appliance, which can be started in VMware Workstation or VMware Server. ACE Server uses LDAP to integrate guest systems into Active Directory and HTTPS for interaction of virtual machines with a server. ACE Management Server is accessed via a thin client. The server side is based on Apache 2.0 web server. To connect virtual environments to ACE Management Server, you should specify a server address when you create a virtual machine. When used in an industrial environment, Management Server collects information about client virtual environments and stores it in SQLite 3 database. A great number of client computers will probably require a large database, which can be provided by Oracle or Microsoft SQL Server. VMware ACE Standard and Enterprise editions are intended to manage up to 50 and 200 clients correspondingly. Additional licenses can be bought any time your requirements in secure environments grow. Bottom lineVMware ACE is a unique virtualization solution from the point of view of creating secure computing environments. Wide opportunities for centralized deployment of virtual machines, including security and data access policies, as well as expiration control give software developers a new way of delivering their products to end users. VMware ACE is also convenient for software demonstrations. And of course, VMware ACE is ideal for deploying a virtual infrastructure of desktops in the industrial environment, which must have tools for protection against unauthorized access. VMware ACE users don't worry about security of their portable virtual environments, even if they are stolen with their notebooks. Out of doubt, VMware ACE has future in the sector of middle and large business, where data protection plays one of the key roles. Write a comment below. No registration needed!
|
Platform · Video · Multimedia · Mobile · Other || About us & Privacy policy · Twitter · Facebook Copyright © Byrds Research & Publishing, Ltd., 1997–2011. All rights reserved. |